Operational security ("OPSEC") in crypto is of paramount importance. Hackers need only one point of weakness in your system to compromise the rest.
This article will serve as an "OPSEC checklist" to ensure a minimum security standard necessary to protect your valuable cryptocurrencies.
Coins Held On Crypto Exchanges
Below is a list of common mispractices out of convenience:
Using the same email for multiple accounts
Using the same password for multiple accounts
Saving screenshots / unencrypted text files of sensitive information ⏤ passwords & recovery phrases ⏤ to iCloud / Dropbox / password managers
2FA authentication activated, but is on the same device (i.e. Google Authenticator extension on Chrome desktop)
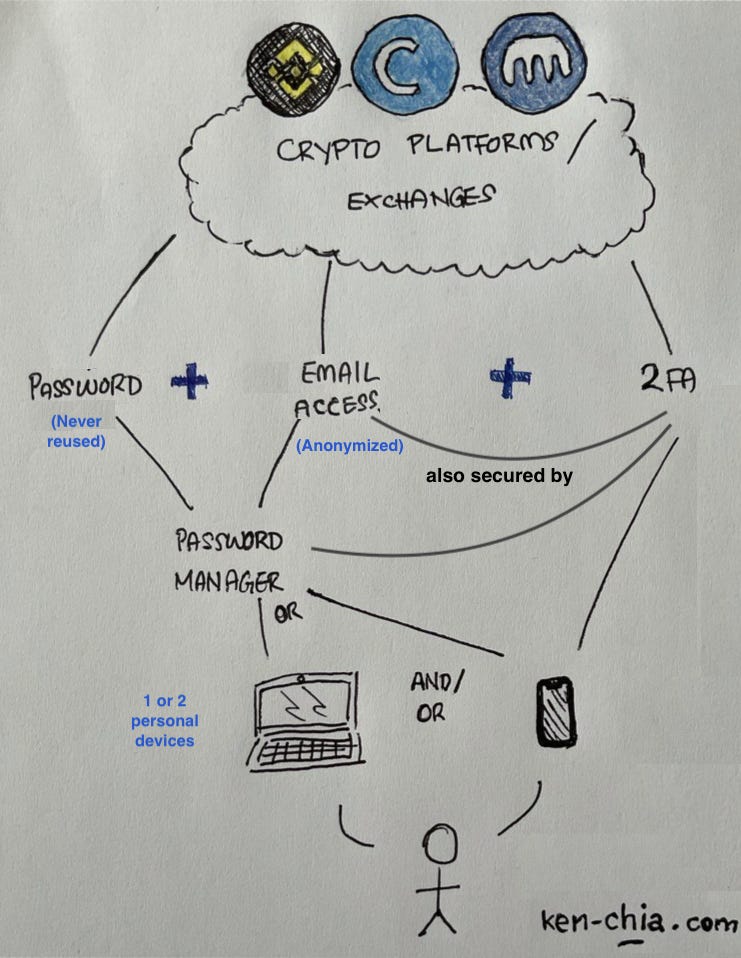
The chart below illustrates how your exchange accounts should be set up:
Crypto exchanges are likely where you first obtain your cryptoassets. The overview above is self-explanatory with the following key principles:
Never reuse any passwords
Secure and anonymize your emails
2FA EVERYTHING (optional but highly recommended: use hardware tokens)
1. Never reuse any passwords ⏤ start using a Password Manager
According to Dashlane's 2017 findings, the average American Internet user has 150 online accounts that require a password–in theory. This implies that you would need to memorize 150 unique, complex passwords for maximum account security.
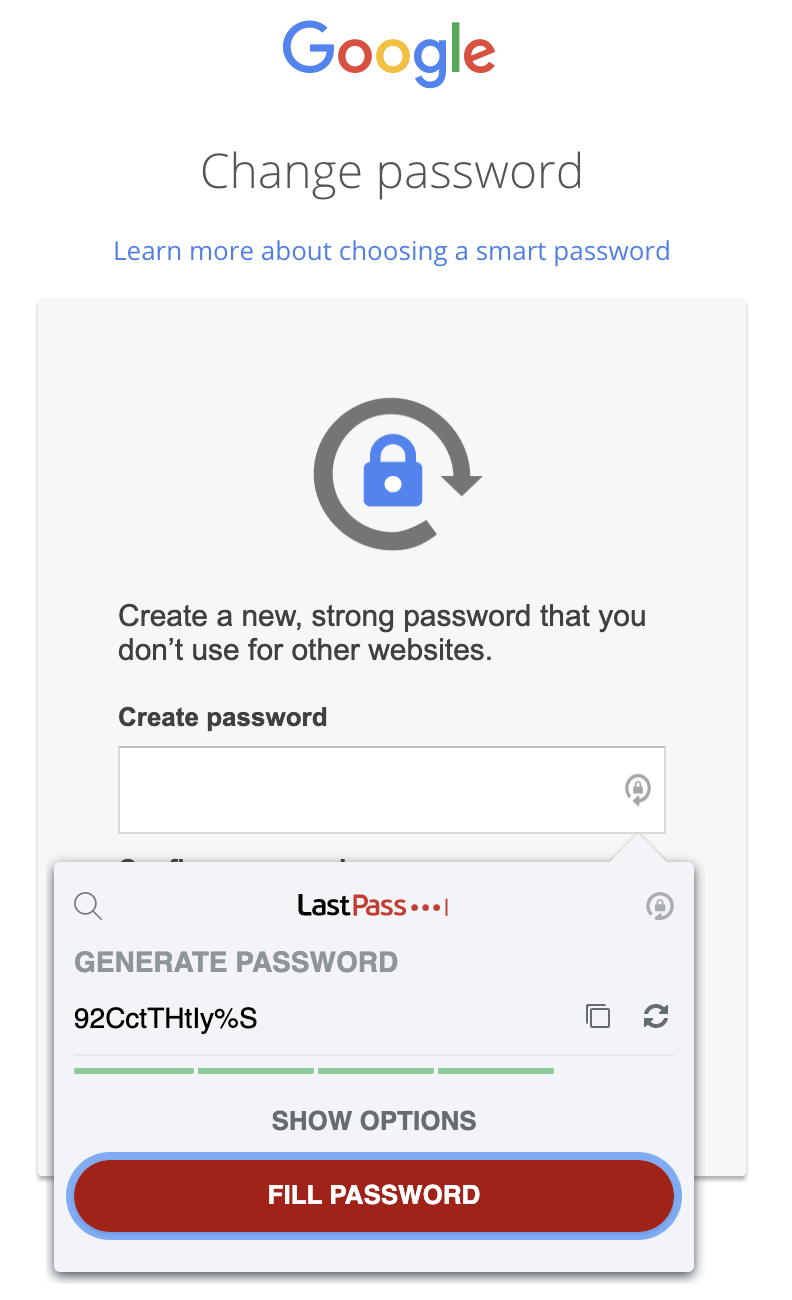
Password managers are great tools to help generate long, secure & unique passwords for all your accounts. There are many available for free / subscription-based ⏤ LastPass and Bitwarden are some of the more popular ones.
Set up LastPass or Bitwarden, create and remember one strong master password ⏤ if you choose to write it down, store the physical copy in a safe location and never save it anywhere online.
This video provides a good framework in creating a strong master password ⏤ it is a lot easier than most think!
Important: No photos, no iCloud, no Evernote. Never save your master password on any device with an Internet connection.
For those who use Chrome / Safari / Firefox built-in password managers ⏤ stop using them.
Built-in password managers in web browsers store your passwords on your computer in an unencrypted format. Remote hackers could technically access the password files on your computer and view them, unless you encrypt your computer’s hard drive.
Here is a good guide to get started with password managers, and a video to explain how they work in greater detail.
I would also recommend using an anonymized email for your password manager, one that you do not use for anything else.
2. Secure and anonymize your emails
i) Use Anonymous Email Addresses. Login credentials typically consist of your password, and email address. Password managers can help us generate unique, complex and long passwords for our valuable accounts ⏤ why not do the same for email addresses?
<randomgibberish>@gmail.com is a lot harder to guess vs <firstnamelastname>@gmail.com
This alone makes your login credentials that much more difficult to be compromised.
ii) Use multiple email addresses. If possible, use a new and unique email for each exchange account (or have a few different emails to mix and match). This way, there is no public linkage between your exchange accounts. This simple practice alone greatly helps compartmentalize OPSEC risks, minimizing damage contagion in the event of a security breach (one compromised email will not affect your other accounts).
iii) Disable secondary email & phone number recovery options. Contrary to popular belief, these actually add more points of weakness in your OPSEC:
"Many email providers offer options to recover access to your email account in case you get locked out or forget your password. Often they allow you to set up a secondary email account for recovery or use the phone number registered to receive a SMS or phone call. Both of these options can be abused and we strongly recommend not setting either of them up. You would be surprised how easy it is to clone a SIM card or for an imposter to call your phone service provider and convince an agent they are speaking with you. If you have your phone number registered on the email account, remove it or turn it off as a recovery option" ⏤ Kraken
Other Options to Consider
Use Google's Advanced Protection Program (free, opt-in). For people whose accounts contain particularly valuable files or sensitive information, i.e. journalists, activists, business executives, and people involved in elections, etc.
Periodically check email account settings and activity logs. Check the device activity page in your email settings to make sure that no unknown devices have logged into your account. Also, check the email forwarding section to make sure that nobody has set up email forwarding to another email address that you are not aware of.
But why go through all these troubles? Consider this:
If a hacker gains access to your main email account, they will be able to control everything: your Facebook, LinkedIn, e-banking, government login portals, crypto accounts and every single account you created using that email.
If they hack into key email accounts, they can literally be you on the Internet.

3. 2FA Everything
Important: Stop using SMS authentication ⏤ especially in the US, the risks of SIM swap attacks are adamant. Even Jack Dorsey's (Twitter CEO) Twitter account was hacked via SIM swap back in 2019.
Instead, use Two-Factor Authentication (2FA) ⏤ either via i) software or ii) hardware tokens.
i) Software Tokens (2FA Apps)
Some of the more popular (and free) authentication apps are Google Authenticator and Authy. Download either one on your mobile device and start enabling 2FA on all supported accounts.
There are several differences between the two, but in general:
Google Authenticator
+ Very simple to use
- Does not allow multi-device sync
- Not possible to protect app via PIN
Authy
+ Secures authentication code with option to use a PIN / biometrics to protect the app
+ Multi-device sync solution (although I would suggest to enable it only when you need to sync another device. Once synced, disable multi-device sync. More here)
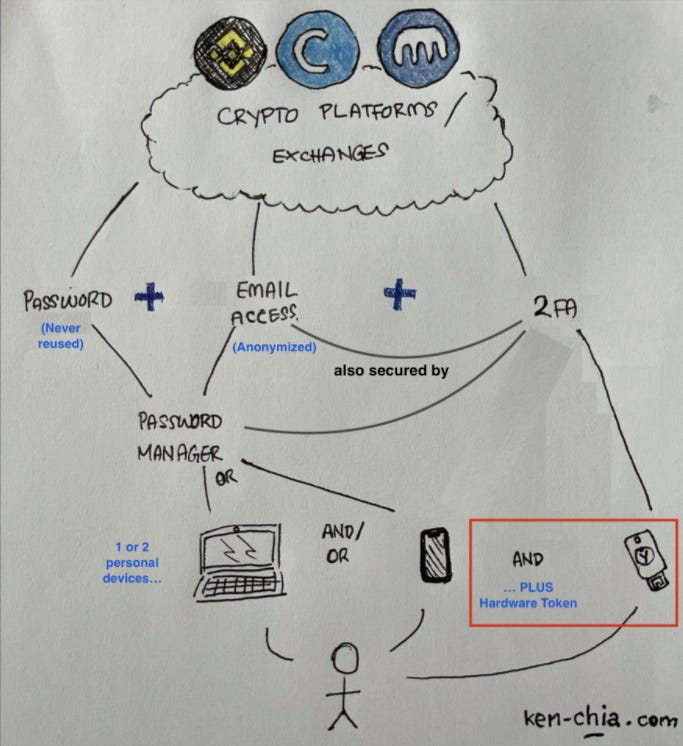
ii) Hardware Tokens (YubiKeys)
If you value your accounts with at least $100 (most of us should), buy at least two YubiKeys and set them up with your key accounts (emails and exchanges).
You need at least two, because if you lose one, you will have at least one other recovery option stored somewhere secure.
With any security tools, only order directly from the official website.
How does it work?
The YubiKey makes 2FA as simple as possible. Instead of a code being texted to you, or generated by an app on your phone, you press a button on your YubiKey ⏤ that's it.
How? Each YubiKey has a unique code built on to it, which is used to generate codes that help confirm your identity. More here.
Which one to buy?
YubiKeys comes in multiple sizes. Personally, I use the YubiKey 5 NFC, which works with both laptops (via USB A or C) and mobile devices (via NFC).
There is even a short quiz on the official website to help you identify which YubiKeys are right for your setup.
For more FAQs on YubiKeys, check out this subreddit or this FAQ.
Why buy at least two?
Things can and will happen in life. Just get a spare. You wouldn't have only one set of keys to your home, would you?
Register the YubiKeys on critical accounts so you don't get locked out if you lose one. Store one somewhere you can easily access daily like a keychain, and at least one other in a safe place (at home, safety deposit box, bank vault etc).
What happens if you lose one? Nothing to worry, because:
i) The person who finds it would likely not know who it belongs to; and
ii) Even if the person knew, they would need to know which accounts you have used it on, AND know your login credentials to those accounts, AND attempt to login before you remove the lost YubiKey from your accounts
If you do end up losing one, use your spare YubiKey to log into your accounts and easily remove the lost key. Immediately order a new replacement YubiKey and set that up once received.
Why are YubiKeys recommended by most cyber security professionals?
All approaches for human authentication rely on at least one of the following:
i) Something you know (eg. a password) ⏤ password manager
ii) Something you are (eg. a fingerprint / Face ID) ⏤ your personal device
iii) Something you have (eg. a 2FA) ⏤ software or hardware
2FA software apps are mostly secure, but they are not unhackable. Adopt this mindset:
Anything and everything stored online (unencrypted) can and will be stolen.
In most cases, it only requires a man-in-the-middle attack via simple social engineering.
Hardware 2FA tokens are strong enterprise tools that are used by top global tech companies like Google for a reason.
Let's see how this fits into our OPSEC overview:
Now, an attacker would need access to one of your personal devices, your login credentials, AND physically have your hardware token.
YubiKey Pros
Simplicity: just tap the device (no installation required, no cumbersome 2FA codes)
Widely supported by most major services (click here for full list)
YubiKey Cons
Not supported by all services (i.e. FTX supports only one YubiKey at a time)
Coins Held Off Crypto Exchanges
Cryptocurrencies are bearer assets. If you keep your coins on an exchange, you are trusting that exchange to keep your private keys (and coins) secure on your behalf, with intermingled funds from all their customers.
From high withdrawal fees, to a growing history of exchange hacks, philosophical beliefs against centralization etc, there are real reasons why you would want to self-custody and hold your own coins.
It is empowering to be able to hold your own coins in your custody so it cannot ever be confiscated or withheld by banks, or exchange hackers. Direct control of your own money. Holding your own coins provides you with unlimited freedom to transact on the blockchain, but at a cost: holding your own keys means being your own bank ⏤ if you lose your keys, no one can help you.
Although it seems straightforward, not everyone should hold their own keys given the surprising amount of nuance to consider.
Most use a combination of the two ⏤ trading portfolio on exchanges (or hot wallets like Metamask), and the rest in personal custody (cold wallets), diversifying counterparty and custody risks.
It is a personal decision. How much do you have? How frequently do you plan to transact? Are you confident that your self-custody setup is more secure than with an exchange / regulated custodian's cold storage?
Let percentage of net worth guide your decision. As a personal rule of thumb, if you have more than 5% of your net worth in crypto, you should at least use a hardware wallet.
The two most popular hardware wallets are Ledger & Trezor.
I would recommend at least two hardware wallets for redundancy (similar to having two YubiKeys). Keep one with you, and a backup in a secure location in case you lose your main device.
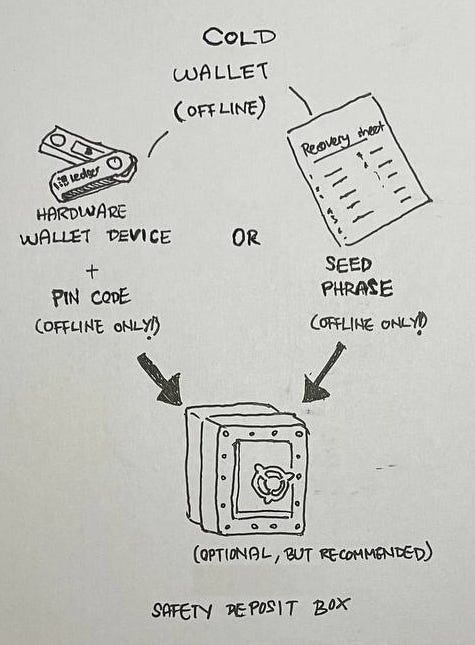
Hardware wallets are capable of generating or importing seed phrases ⏤ strings of 12 or 24 words which are literally the keys to your coins.
If you lose your hardware wallet, you can still key in your seed phrase into a new replacement hardware wallet to access your coins.
However, if you lose your hardware wallet AND your seed phrase instead, your coins are as good as gone.
Here are some best practices in handling seed phrases:
Write it down on the provided recovery sheet that comes with your hardware wallet, and store it in a secure place. NEVER take a picture of it, save it on a device, sync to cloud etc ⏤ remember: "anything and everything stored online (unencrypted) can and will be stolen"
Consider a metal solution to durably store your seed phrase
Never key it into a computer / mobile device with an Internet connection. It should always remain offline, and only keyed into secure offline devices like hardware wallets
Never lose it! You can lose your hardware wallet device but you cannot lose your seed phrase
Advanced Security Principles (at your own risk)
Splitting the seed phrase into several parts stored in different locations
Adding your own custom 25th phrase
How secure are seed phrases? Although it seems like only 24 regular English words, the number of possible permutations is so large that there is no English word for the number! To give an idea, this number is larger than the number of atoms in the entire universe (see line 24 below):

Hence, the odds of two people picking the exact same 24 words in the exact same order is virtually zero.
For a more detailed explanation on hardware wallets and seed phrases, this article is a good resource.
Important final note: Don't make your custody setup so complicated that even you forget how to access the funds. Go slow, test with small amounts and add more as you get more comfortable. Test your setup periodically.
Additional OPSEC tips
Never log into your key accounts on a shared device. You never know if the device has been compromised or not
If you absolutely have to use public WiFi, use a VPN
As a handy reminder, I have summarized our OPSEC 101 in the following Twitter thread:


Invest The Time
Some of these measures might seem like overkill to most people.
In crypto, these are not good-to-haves ⏤ these are must-haves. Hackers only need one point of failure.
Your cyber / crypto security is as good as its weakest link. Invest the time to set up your OPSEC right once and for all.
Especially in crypto, we need to upgrade our attitude and culture towards security.
Disclaimers: I only recommend products that I would use myself. This post may or may not contain affiliate links that at no additional cost to you, I may earn a small commission. Depending on the platform, you may receive rewards too. Nothing written on ken-chia.com is financial advice.